
by Kevin Justus | Dec 10, 2024 | Cybersecurity
There are many types of malware. One of the most common is called “malvertising.” It crops up everywhere. Including social media sites and websites. You can also see these malicious ads on Google searches.Two things are making malvertising even more dangerous. One is...

by Kevin Justus | Dec 5, 2024 | Cybersecurity
Today’s businesses are no stranger to the word cybersecurity. They are facing a growing wave of cyberattacks. These come from ransomware to sophisticated phishing schemes. How do you stand ahead of these threats? A strong cybersecurity strategy is essential. One...

by Kevin Justus | Nov 5, 2024 | Cybersecurity
Email is a fundamental communication tool for businesses and individuals alike. But it’s also a prime target for cybercriminals. Cyberattacks are increasing in sophistication. This means enhancing your email security has never been more critical.Ninety-five percent of...

by Kevin Justus | Oct 10, 2024 | Cybersecurity
Your smartphone is a digital wallet, communication hub, and personal assistant. All rolled into one portable device. It’s packed with sensitive data, from financial information to personal photos. This makes it a prime target for cybercriminals. Mobile malware is...

by Kevin Justus | Sep 15, 2024 | Cybersecurity
Traveling with technology has become a necessity. Whether for work, communication, or entertainment, we rely heavily on our devices. But traveling exposes these gadgets to various risks. Theft, damage, and loss are common concerns. We’ve put together some helpful...
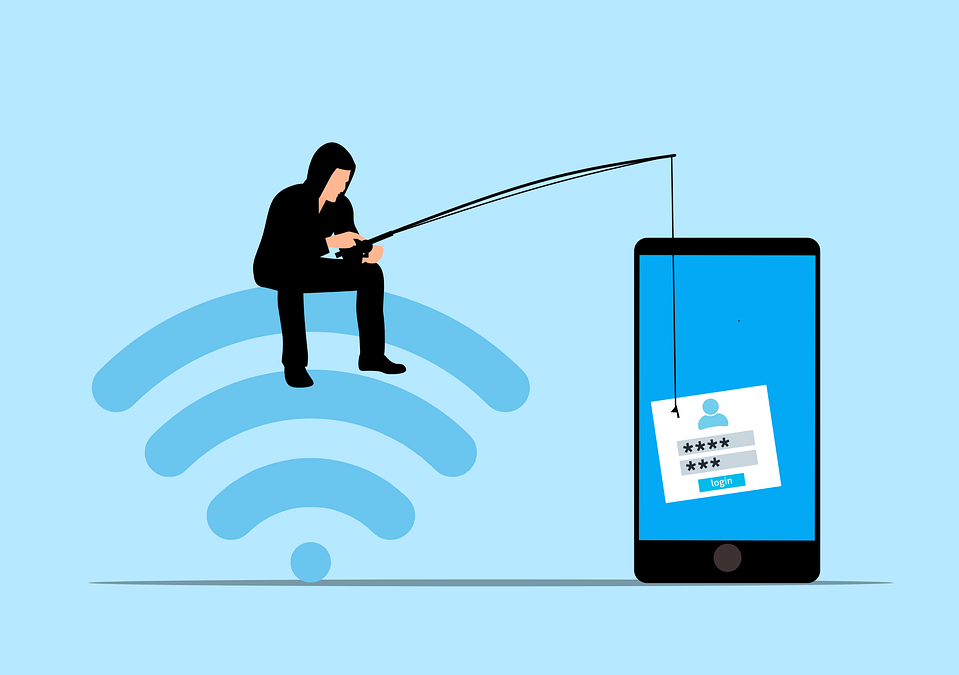
by Kevin Justus | Aug 30, 2024 | Cybersecurity
Phishing has always been a threat. Now, with AI, it’s more dangerous than ever. Phishing 2.0 is here. It’s smarter, more convincing, and harder to detect. Understanding this new threat is crucial. A recent study found a 60% increase in AI-driven phishing...







